Project: Upgrading RSA keys to Ed25519
Generating new SSH key with Ed25519
greys@maverick:~/.ssh $ ssh-keygen -o -a 100 -t ed25519 -C “[email protected]”
Generating public/private ed25519 key pair.
Enter file in which to save the key (/Users/greys/.ssh/id_ed25519):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /Users/greys/.ssh/id_ed25519.
Your public key has been saved in /Users/greys/.ssh/id_ed25519.pub.
The key fingerprint is:
SHA256:SVcxool+HpvZ4ufzSIh4mzmTw1Rm/7c9+8xh01DByh4 [email protected]
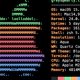
The key’s randomart image is:
+–[ED25519 256]–+
| . +… |
| . o o . ..|
| . + . . . .|
| . .+o E . |
| .+S. . o |
| ..+ B. . ..|
| .oo.B o. +.|
| .*= oo.. o=o|
| ++.ooo…oO|
+—-[SHA256]—–+
Deploying new key to existing servers
greys@maverick:~/.ssh $ ssh-copy-id -f -i id_ed25519 becky
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: “id_ed25519.pub”
Number of key(s) added: 1
Now try logging into the machine, with: “ssh ‘becky’”
and check to make sure that only the key(s) you wanted were added.
Checking new key with servers
greys@maverick:~/.ssh $ ssh -vvv -i id_ed25519 becky
And here’s the fragment of the output confirming we’re indeed using id_ed25519:
debug1: Next authentication method: publickey
debug1: Offering public key: id_ed25519 ED25519 SHA256:SVcxool+HpvZ4ufzSIh4mzmTw1Rm/7c9+8xh01DByh4 explicit agent
debug3: send packet: type 50
debug2: we sent a publickey packet, wait for reply
debug3: receive packet: type 60
debug1: Server accepts key: id_ed25519 ED25519 SHA256:SVcxool+HpvZ4ufzSIh4mzmTw1Rm/7c9+8xh01DByh4 explicit agent
debug3: sign_and_send_pubkey: ED25519 SHA256:SVcxool+HpvZ4ufzSIh4mzmTw1Rm/7c9+8xh01DByh4
debug3: sign_and_send_pubkey: signing using ssh-ed25519
That’s it for this week. It’s been a fun project!