How To: Change Passphrase for SSH Private Key
 Change Passphrase ssh-keygen -p
Change Passphrase ssh-keygen -p
If you need to change or add a passphrase to your existing SSH private key just use ssh-keygen, the same tool which creates the key in the first place. Add the -p option to specify you want to change an existing private key’s passphrase instead of creating a new private key.
Changing SSH key passphrase
Here’s the simplest version of this command, resulting in changing the passphrase of the current user’s private key, stored in ~/.ssh/.
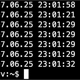
As you can see, you’re asked to confirm the location of the SSH key file, they asked for old passphrase and asked twice for the new passphrase:
greys@server:~$ ssh-keygen -p
Enter file in which the key is (/home/greys/.ssh/id_rsa):
Enter old passphrase:
Enter new passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved with the new passphrase.If you have your key elsewhere or have multiple SSH keys, use the -f option followed by the path to the key file:
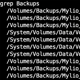
greys@server:~$ ssh-keygen -f /home/greys/.ssh/id_rsa2 -pIf you have an existing passphrase ssh-keygen will first ask you to enter that before allowing you to set the new passphrase, and if you haven’t had a passphrase before then it will just allow you to set one.
Adding passphrase to an unencrypted SSH key
Sometimes you have unenrypted SSH private keys. That’s a very bad practice, so you should use ssh-keygen -p to encrypt them as soon as possible.
When we encrypt SSH keys, the risk of SSH key stolen remains the same (still just as easy to copy id_rsa file), but the likelihood of it actually being used is minimised because the key will be encrypted with the passphrase that only you know.
When the SSH key isn’t encrypted, ssh-keygen -p command will not ask for the old passphrase:
greys@server:~$ ssh-keygen -p
Enter file in which the key is (/home/greys/.ssh/id_rsa):
Enter new passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved with the new passphrase.Removing passphrase from an SSH key
As bad a practice as it is, removing passphrase protection and encryption from a private SSH key is sometimes necessary, usually when you need to export/import your key into a different keystore.
Use ssh-keygen -p command to remove the passphrase – just press Enter when asked for the new passphrase without typing any phrase.
No Way To Recover Forgotten Passphrase
IMPORTANT: you cannot overwrite a forgotten passphrase. If your SSH key is encrypted, you must have the original passphrase to decrypt the key and save it with the new passphrase. If passphrase is lost, you can’t decript the key so access to it is lost until you recover the passphrase.
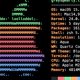
Here’s how it will look if you type wrong passphrase:
greys@server:~$ ssh-keygen -p
Enter file in which the key is (/Users/greys/.ssh/id_rsa):
Enter old passphrase:
Failed to load key /Users/greys/.ssh/id_rsa: incorrect passphrase supplied to decrypt private keySee Also
- How To: Generate SSH key
- How To: Change SSH key passphrase
- SSH port
- SSH port forwarding
- How To: Inspect SSH key fingerprints
- SSH